Introduction
OCI is a cloud computing service provided by Oracle Corporation. It has a plethora of features that allow you to create anything you want on the cloud.
Getting access to your own instance of OCI is simple and free. You can register for a free trial at https://cloud.oracle.com. You will be prompted for a valid credit card, but the card will not be charged at the end of the trial unless you explicitly opt-in.
Every environment has both Pros & Cons, and this implies to the Cloud environment as well. Failure in securing the cloud environment result in external Threat and loss of Data and compromise of infrastructure.
Organizations may lessen the risk of security threats for cloud workloads with the aid of Oracle Cloud Infrastructure (OCI) Security. Oracle enables clients to quickly embrace and secure their cloud infrastructure, data, and apps with the help of easy, prescriptive, and integrated security capabilities built into the OCI platform.
Security Best Practices
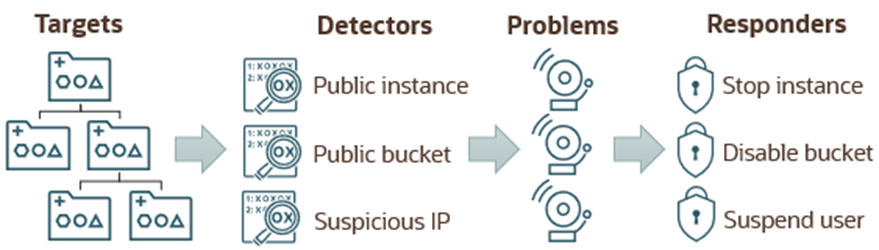
Cloud Guard
Cloud Guard detects misconfigured resources and insecure activity within a tenancy and provides security administrators with the visibility to resolve these issues. Upon detection, Cloud Guard can suggest, assist, or take corrective actions to mitigate these issues. Cloud Guard should be enabled in the root compartment of your tenancy with the default configuration, activity detectors, and responders.
Restrict Resource Movement:
This policy will not let any user move any resource (block volume, compute, database, networking, object storage, etc.) from the security zone compartment to a standard (non-security zone) compartment. Also, a resource from a standard compartment can’t be moved into a security zone unless it satisfies all security zone policies.
Restrict Resource Association:
This policy will ensure that all the individual components (or resources) you are putting together to build your secure infrastructure are selected from within the security fortress. The individual resources like block volumes, compute instances, OSS buckets, databases, networking, etc.,
Deny Public Access:
This policy makes sure all resources are private by denying any internet gateways, public buckets, etc. Restricting public access will give peace of mind to many organizations out there.
Require Encryption:
By default, Oracle encrypts all the data at rest with Oracle-managed keys. This policy enforces Customer Managed Keys by utilizing Oracle Cloud Vault service for block volume and object storage.
Ensure Data Durability:
This policy will deny any database resources without any automatic backups configured.
Ensure Data Security:
This policy focuses on the databases by ensuring that a database can’t be created in a standard compartment by sourcing from a clone or backup of a database in the security zone.
Oracle Approved Images:
This policy ensures that all compute and database resources created in the security zone are sourced from Oracle-approved platform images.
Network Sources A network source is a set of defined IP addresses. The IP addresses can be public IP addresses or IP addresses from VCNs within your tenancy. After creating the network source, it can be referenced in an IAM policy to control access based on the originating IP address.
OCI Security Audit
The Oracle Cloud Infrastructure Vulnerability Screening Service regularly scans compute instances and container images for potential vulnerabilities to assist strengthen the security posture.
There are several ways to conduct security assessments, including using tools and manually reviewing services in accordance with security requirements.
To manage their environment’s security posture, cloud security providers offer built-in capabilities. The restricted functionality of these tools calls for the use of third-party solutions. Below listed are a few third-party tools for scanning and securing OCI.
CloudSploit Scans (https://github.com/cloudsploit/scans)
CloudSploit scans is an open-source project designed to allow the detection of security risks in cloud infrastructure accounts. These scripts are designed to return a series of potential misconfigurations and security risks.
It’s a great tool that supports AWS, Azure, GCP, and even the Oracle cloud assessments.
ScoutSuite – formerly Scout2 (https://github.com/nccgroup/ScoutSuite)
Scout Suite is an open-source multi-cloud security-auditing tool, which enables security posture assessment of cloud environments. Using the APIs exposed by cloud providers, Scout Suite gathers configuration data for manual inspection and highlights risk areas. Rather than going through dozens of pages on the web consoles, Scout Suite presents a clear view of the attack surface automatically.
It supports AWS, Azure, GCP, Oracle, and even Alibaba clouds!
Resources Manual Assessment
https://hub.steampipe.io/mods/turbot/oci_compliance/controls/benchmark.cis_v110
https://www.cisecurity.org/benchmark/oracle_cloud
https://docs.oracle.com/en/solutions/oci-security-checklist/security-controls.html
References
https://akanuri.medium.com/oci-operations-d8ba3fe79be9
https://docs.oracle.com/en-us/iaas/Content/Security/Concepts/security_features.htm