
Though more router manufacturers are making routers easier to set up and configure—even via handy little apps instead of annoying web-based interfaces—most people probably don’t tweak many options after purchasing a new router. They log in, change the name and passwords for their wifi networks, and call it a day.
While that gets you up and running with (hopefully) speedy wireless connectivity, and the odds are decent that your neighbor or some random evil Internet person isn’t trying to hack into your router, there’s still a lot more you can do to boost the security of your router (and home network).
Advertisement
Before we get into our tips, one quick caveat: Wireless routers all have different interfaces, different ways they name their settings, and different settings you can adjust. For this article, I’ll be poking around the interface of a TP-Link Archer C7. You’ll want to explore around your router’s web-based configuration screen (or app) to make sure you’ve adjusted all the right settings, but it’s possible you won’t be able to do everything we’ve detailed below.
Accessing your router’s settings
If your router doesn’t have an easy-to-use app for configuring its settings—like what you typically encounter when buying a mesh-networking system—you’ll probably access its settings by pulling up a web browser (on a device that’s connected to your router) and typing in your router’s IP address:
- On a Windows system, pull up the command prompt and type in
ipconfig. The IP address that’s listed as your default gateway is likely your router’s IP address. - If you’re on a Mac, pull up System Preferences > Network, and click on Advanced in the bottom-right corner. Click on the TCP/IP option toward the top of the next window and look for your router’s IP address.
- If you’re on your iPhone, tap on Settings, then Wi-Fi, and tap on the “i” icon next to the wifi network you’re connected to. Your router’s IP address should be listed right there.
Step One: Update your firmware
Some routers bury firmware updates deep in their settings menus; some might even notify you about a new firmware update the moment you log into their apps or web-based user interfaces. However you find the option, you’re going to want to make sure that your router is running the most up-to-date firmware.
Advertisement
If you’re lucky, your router will be able to download new firmware updates directly from its manufacturer. You might have to click on a button (or two) to start this process, or this might happen automatically—routers that do the latter are great, because most people don’t really think about “checking to see if my favorite tech gear has updated firmware” on a regular basis, if ever.
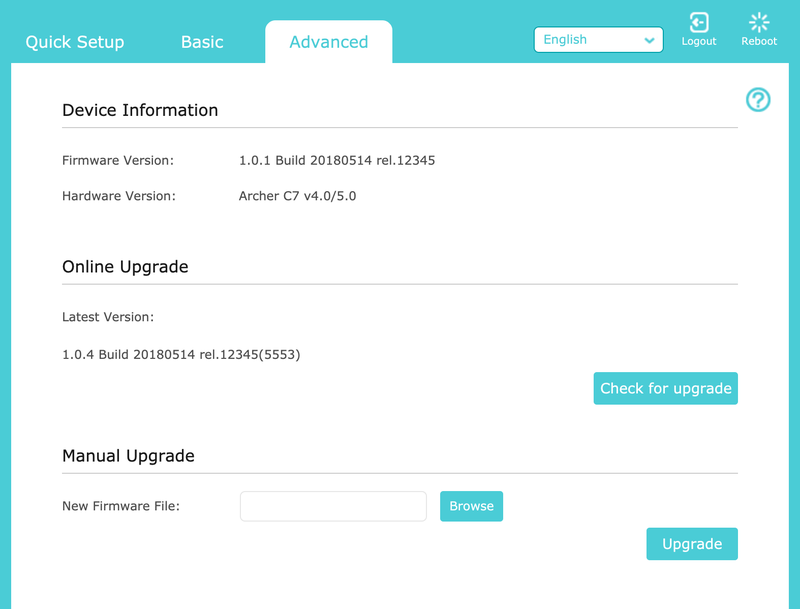
It’s also possible that your router will require you to upload new firmware yourself. If so, you’ll have to download the right firmware from the router’s manufacturer—likely on a support page for your router—and manually update the router by browsing for this firmware file and starting the update process yourself. You’ll have to do this each time you want to update your router with new firmware, which means you’ll have to check for new firmware fairly regularly, perhaps a few times a year. It’s a laborious process that’s easily forgotten, but it’s also important if you want to keep your router protected from external threats.
Change your router login and password
If you’re still using “admin / admin,” “admin / password,” or some variant of generic words to log into your router, change that. Even if your router manufacturer has given you a quirkier password that presumably differs for everybody, it’s important to use a login and password that’s tough to guess or brute-force.
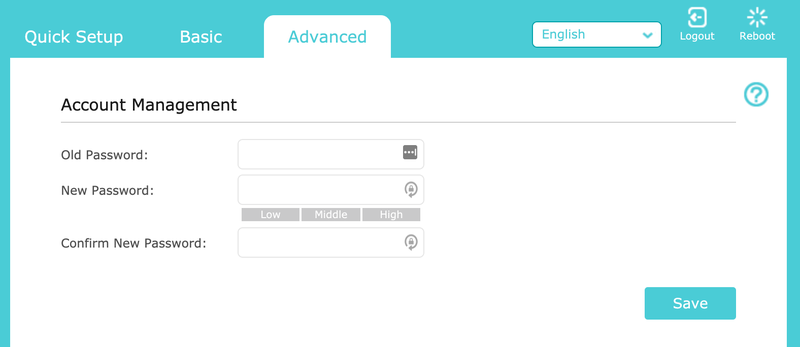
Even if you’re stuck using “admin” as a user name to log in, make your password something complex, not something anyone can look up via a quick web search.
Use WPA2 to secure your wireless network
It almost goes without saying, but don’t use WEP when you’re setting up a password for your wifi network. Passwords “protected” with the WEP encryption are a lot easier to brute-force attack than those encrypted with WPA2. Even though you probably don’t have someone hanging out on your street corner, wardriving everyone’s wireless networks, there’s no reason to not use the stronger WPA2 protocol—unless you have an old device that simply can’t handle WPA2, which is unlikely. And whatever you do, don’t run an open (password-free) wifi network. My god.

Turn off WPS
On paper, WPS—or Wi-Fi Protected Setup—sounds great. Instead of having to type in a long, reasonably complex wifi password on a device, you can just type in a smaller PIN number, likely printed directly on your router.
Advertisement
Guess what? These PIN numbers are much easier to brute-force attack than a more complicated password or passphrase. While a number of routers will time out an attacker after they botch a certain number of password attempts, that hasn’t stopped more ingenious WPS attacks from surfacing. The easiest way to prevent these kinds of shenanigans is to just disable WPS entirely.
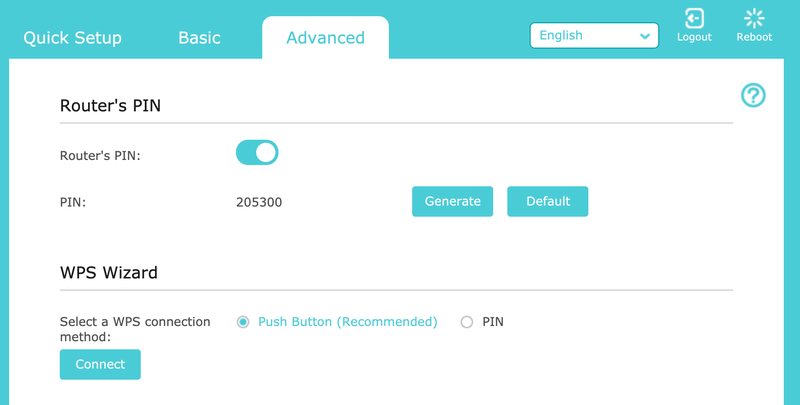
Yes, you’ll have to type in your password. Yes, it’ll be annoying. It’s an extra minute of your life. You’ll be fine. Or, if you truly cannot handle this process, check to see if your router allows you to use push-button WPS instead of PIN-based WPS. That way, you’ll have to physically press buttons on your router and any devices you want to connect, which will make it a lot trickier for someone to exploit WPS and break into your network.
Use a better DNS
Browse the web a little bit faster by switching away from your ISP’s DNS and using a service like Google DNS, Cloudflare, or OpenDNS. As an added bonus, you’ll also increase the likelihood that you actually make it to the websites you’re trying to visit without any man-in-the-middle attacks, popups, redirects, interstitials, or annoying “you made a typo in your web address so we’re going to redirect you to a webpage filled with spam and ads” that your ISP might use.
Advertisement
If you want to get really crafty, you can drop a service like OpenDNS on your kid’s laptop, enable parental controls to keep them off time-sucking websites like Tumblr and Reddit, and give yourself a different DNS provider (like Google DNS) to browse the web without any restrictions. Your child will hate you, but at least they’ll turn out to be a rocket scientist with 27 inventions instead of a Twitch streamer with 3 followers.

Consider using MAC filtering, annoying as it might get
While it’s easy for an attacker to spoof a MAC address, you can at least give yourself a little extra security by setting up your router to only allow devices to connect that appear on a whitelist. This filtering is based on each device’s MAC address—a long string of letters and numbers that looks something like “00-11-22-33-44-55.”
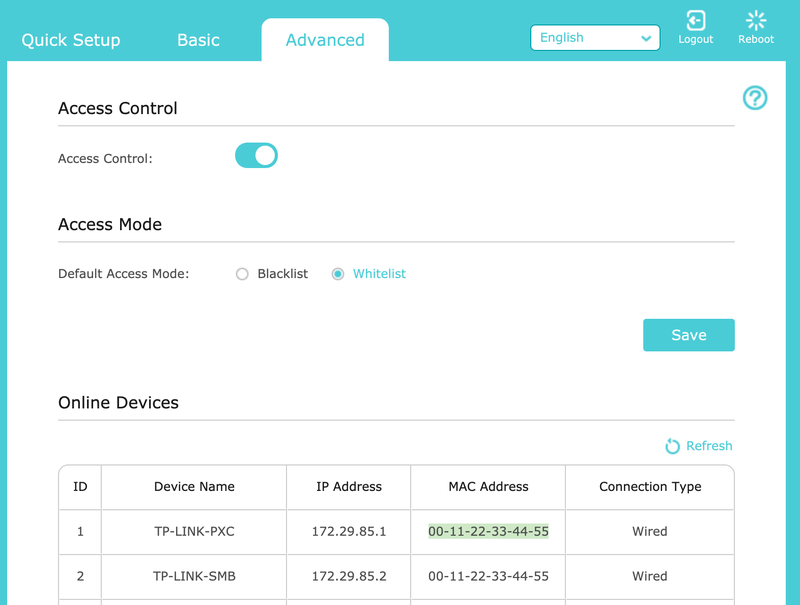
While this means that you’ll need to go in and add any new devices you purchase whenever you want them to be able to connect to your router, it also means that devices you don’t authorize won’t be able to do squat. Like I said, though, MAC addresses are easy to spoof, so if this tip gets more annoying than practical, feel free to disable MAC filtering. You’ll be OK.
Consider scheduling your wifi
If you work a pretty normal schedule during the week and you have no reason to remotely connect to your home devices, consider using your router’s scheduling mechanism—if it has one—to just turn off your wifi when you aren’t home.
Advertisement
This isn’t the most practical tip if you have a bunch of smarthome devices that need the Internet, like if you want to be able to turn the lights on and off to piss off your cat or you want to be able to watch a delivery driver drop off the expensive package you ordered. If you live a relatively simple life—no harm there—and nothing really needs Internet connectivity when you aren’t around, then why power up your wifi for no reason? It’s hard to hack into a network that doesn’t exist.
Disable potentially sketchy services
You probably don’t need to mess with your router’s settings when you aren’t actively connected to your wireless network. If your router has some kind of an option for “remote management” or “remote administration” make sure it’s disabled.
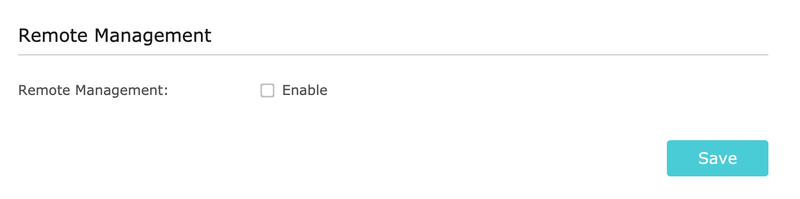
You should also consider disabling UPnP on your router, although this might give you a little grief when you’re gaming or running BitTorrent—to name two examples. Still, when an entire website is dedicated to the various ways one can exploit UPnP for nefarious purposes … maybe it’s time to go back to manually forwarding ports, if needed.
Advertisement
Some routers also let you set up an FTP server so you can transfer files in and out of your network. However, we live in an era when it’s easy to use any number of cloud storage providers—or file-uploading services—to share your files. You probably don’t need to run an FTP at home, and it’s a lot safer to disable this feature entirely (if your router supports it).
You also likely don’t need to access your router over SSH or Telnet—turn either off, if offered—nor do you probably need to access any USB-connected printers or storage when you aren’t at home. In short, if your router lets you do something from afar, consider turning the feature off (if you can). The fewer ways you can access your home network when you aren’t in it, the harder it’ll be for someone else to take advantage of a vulnerability and access your router (or your home network).
If you can, consider disabling your router’s cloud functionality as well. While it might be useful to be able to edit your router’s settings by logging into the manufacturer’s cloud service, it’s just one more open door that an attacker could use to compromise your router (or network). While you have no choice with some routers—typically mesh routers—it’s always better, and safer, to log into a router’s web-based UI manually from a device that’s connected to your home network, even though it’s a lot less convenient.
Consider a separate wifi network for guests and smart-home devices
I’ve been playing, testing, and reviewing routers for more than a decade, and I still have yet to meet someone who uses their router’s guest network feature. Heck, I don’t think I’ve ever even connected to a friend’s “guest network” in their home or apartment.
Advertisement
Still, the premise of a guest network is great, security-wise: Your router automatically sets up a second SSID for friends to use, and any device connecting to it is walled off from other devices on your primary network, either plugged into your router directly or connected wirelessly. (Most routers let you adjust whether you want guests to see everything, each other, or nothing, if you need to customize your setup a bit.)
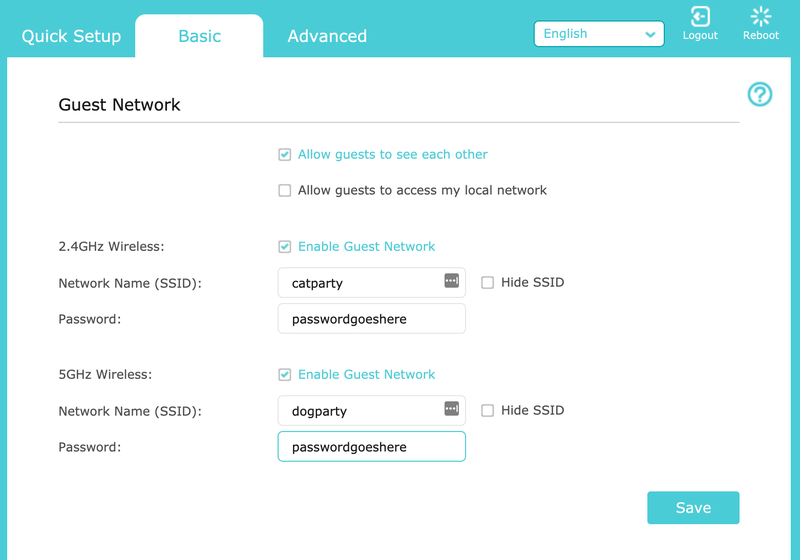
A guest network comes with an added bonus, too; you can use it for all of your less-secure smart-home devices. If someone takes advantage of a vulnerability in your smart lightbulb and breaks into your network, there will still be a layer of protection between your hacked device and your desktop PC, smartphone, and laptop—to name a few examples. While you can also get crazy and segment off your network with separate SSIDs and VLANs, if your router supports it, this is an easier method that won’t give you a weekend’s worth of headaches (if you don’t know what you’re doing).
Read the Full Article here: >Lifehacker









