Users of Google Chrome Canary, the cutting edge version of Google’s web browser, have a chance to get a sneak peek of a user interface design refresh that Google may plan to launch in all versions of Chrome eventually.
The feature is hidden behind a flag currently but that is a common practice by Google; the company uses flags to hide future features from the general population. While there is no guarantee that features will land in Chrome one day, it is often the case that Google uses experimental flags to prepare the wider release.
Chrome’s user interface has not changed all that much throughout the years. Google started a Material Design refresh of internal Chrome pages in 2015 and the process is still ongoing. The company changed the design of the Settings page in mid-2017, and the flags page in the end of 2017.
Google Chrome’s UI design refresh
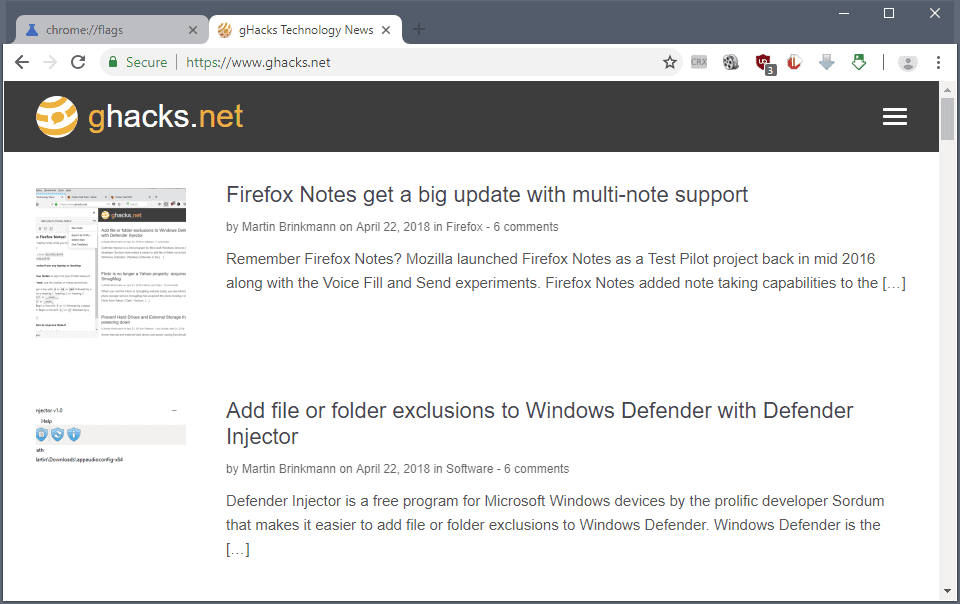
The screenshot above shows the new refreshed Material Design front user interface of Google Chrome. The very first thing you may notice is that Chrome’s tabs are slightly rounded now instead of sharp edged.
Tabs retain the rounded look even if you create a tab overload situation in Chrome when you open too many tabs so that each is displayed without any site indicator (as Chrome does not use scrolling in the tab bar).
The tabbar itself has a white background now. Inactive tabs are displayed with gray text on a gray background, the active tab with gray text on a white background.
There are other changes:
- The design of the New Tab button changed to a plus icon.
- The Chrome address bar has round edges, and its background is set to gray and not white anymore.
- The profile indicator was moved from its original position near the window controls to the main Chrome toolbar.
How to enable the design refresh

You need to run Chrome Canary (version 68 or later) on Windows right now to enable the refresh. If the design refresh is not pulled again, it will become available for Mac or Linux as well in the future.
- Load chrome://flags/#top-chrome-md in the Chrome’s address bar. The address opens the experimental page of Chrome.
- The preference UI Layout for the browser’s top chrome determines the user interface design. Click on the menu next to it and select Refresh.
- Restart Google Chrome.
You can undo the change at any time by setting it to the default value. Other values that are supported:
- Normal — clamshell devices.
- Hybrid — for devices with touchscreen.
- Touchable — new unified interface for touch and convertibles.
- Auto — unclear.
Closing Words
The UI design refresh of Chrome is a work in progress. While it is likely that Google is going to launch a refresh of the design eventually, it is possible that it will look different from the first version that popped up in Chrome Canary in the past days.
Mozilla, maker of Firefox, moved away from rounded tabs with the release of Firefox 57.
Now You: what is your take on the new UI design?
Summary
Article Name
First look at Google Chrome’s UI design refresh
Description
Users of Google Chrome Canary, the cutting edge version of Google’s web browser, have a chance to get a sneak peek of a user interface design refresh that Google may plan to launch in all versions of Chrome eventually.
Author
Martin Brinkmann
Publisher
Ghacks Technology News
Logo
Read the Full Article here: >Top 100 Network Security Tools