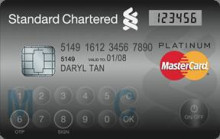
Two-factor authentication just got a whole lot more convenient for residents of Singapore, after Standard Chartered Bank’s local outfit teamed with MasterCard to offer account-holders a credit card that is also a one-time-password-generating hard token.
MasterCard calls the device a ‘Display Card’ and says it includes “an embedded LCD display and touch-sensitive buttons”.
Original news article at https://news.hitb.org/ on November 08, 2012 at 07:53AM